Breathtaking Tips About How To Avoid Mysql Injection

In fact, sql and other injection types are #1.
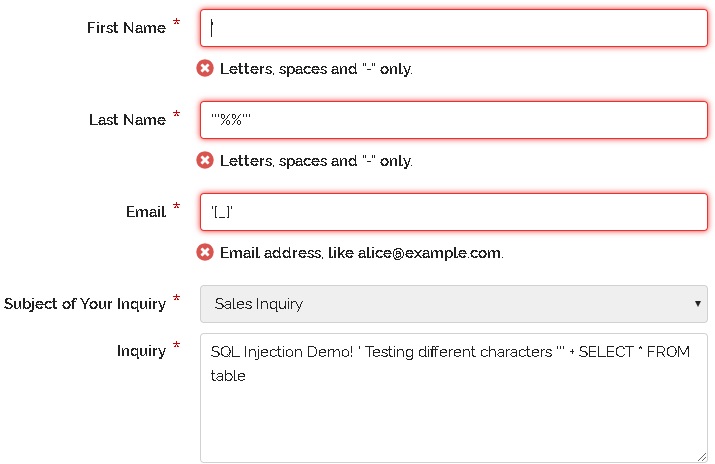
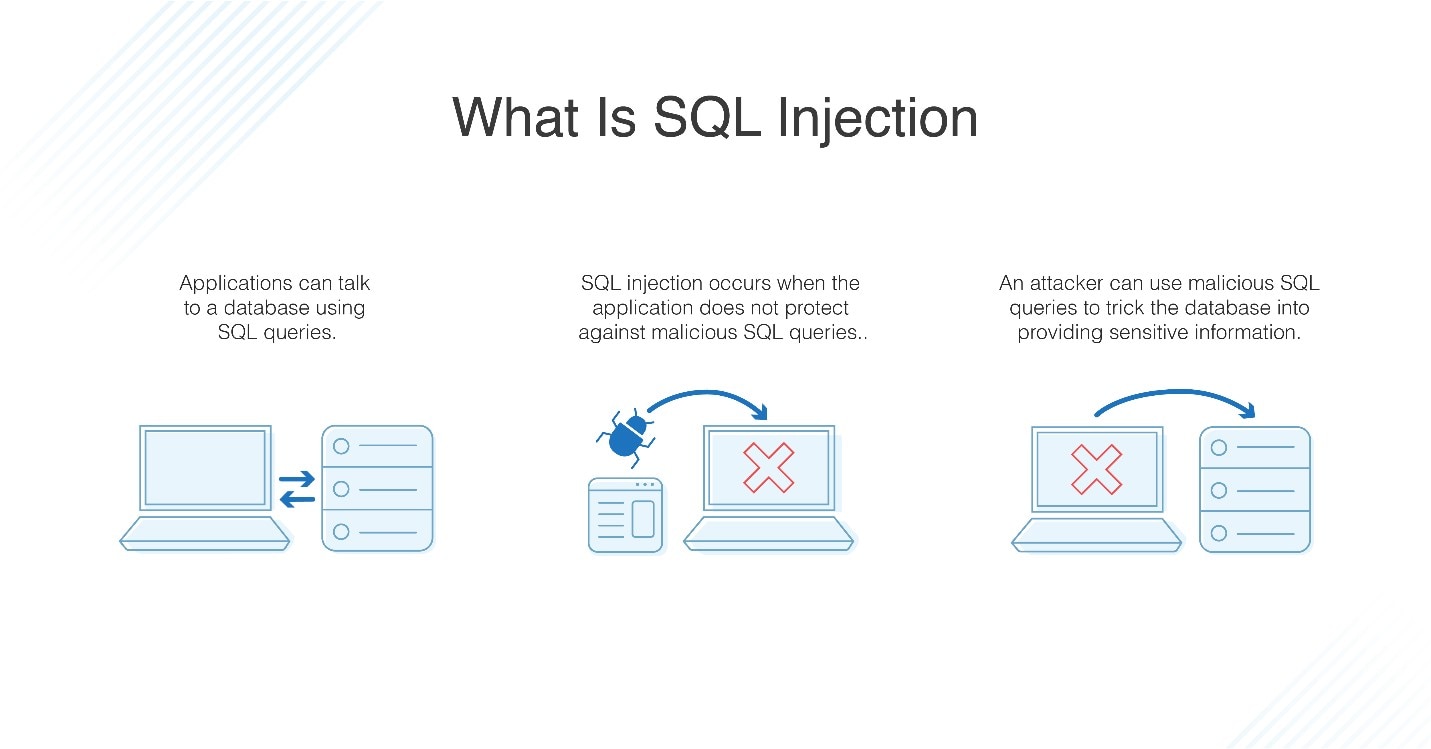
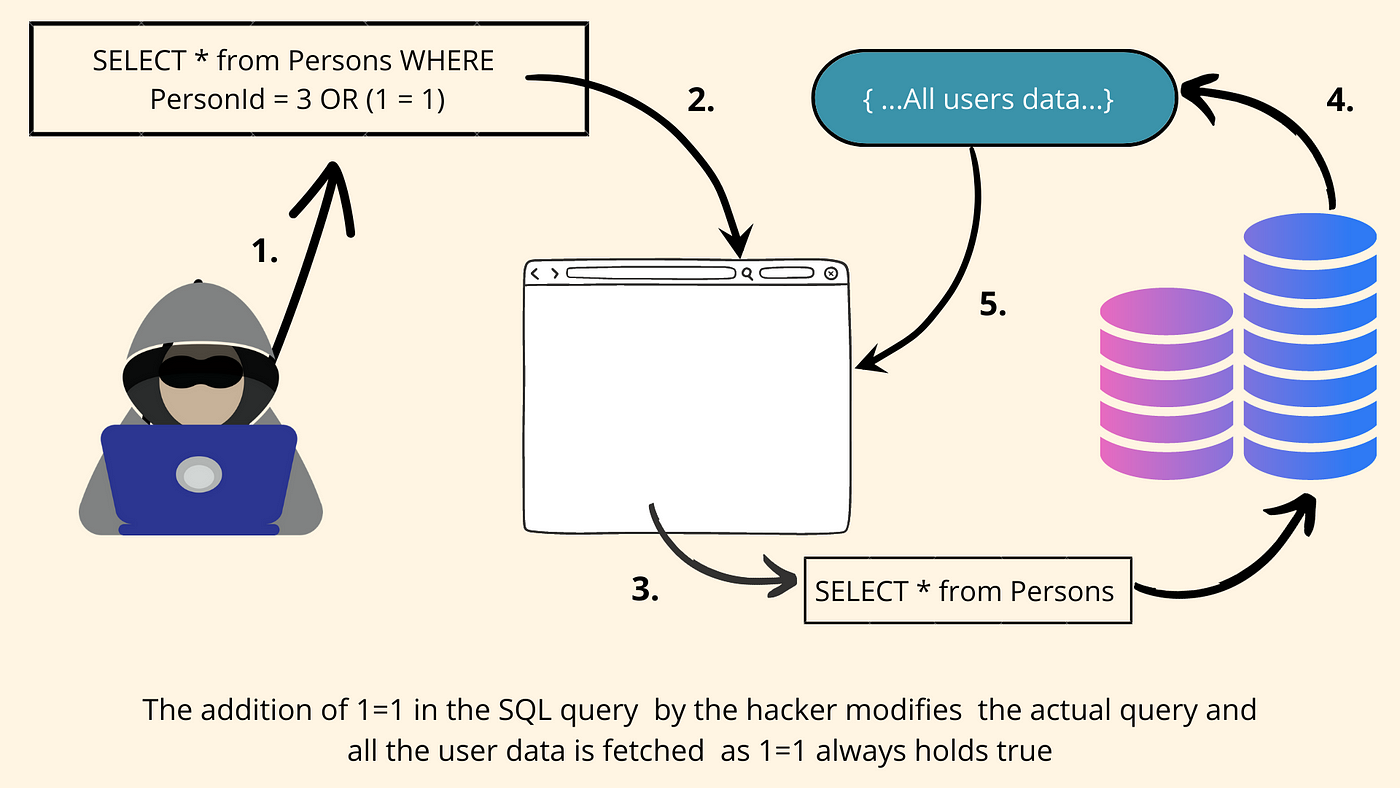
How to avoid mysql injection. Check if mysql installed successfully; Now to avoid this type of sql injection, we need to sanitize the password input and username input using mysqli_real_escape_string() function. Sql injection based on 1=1 is always true.
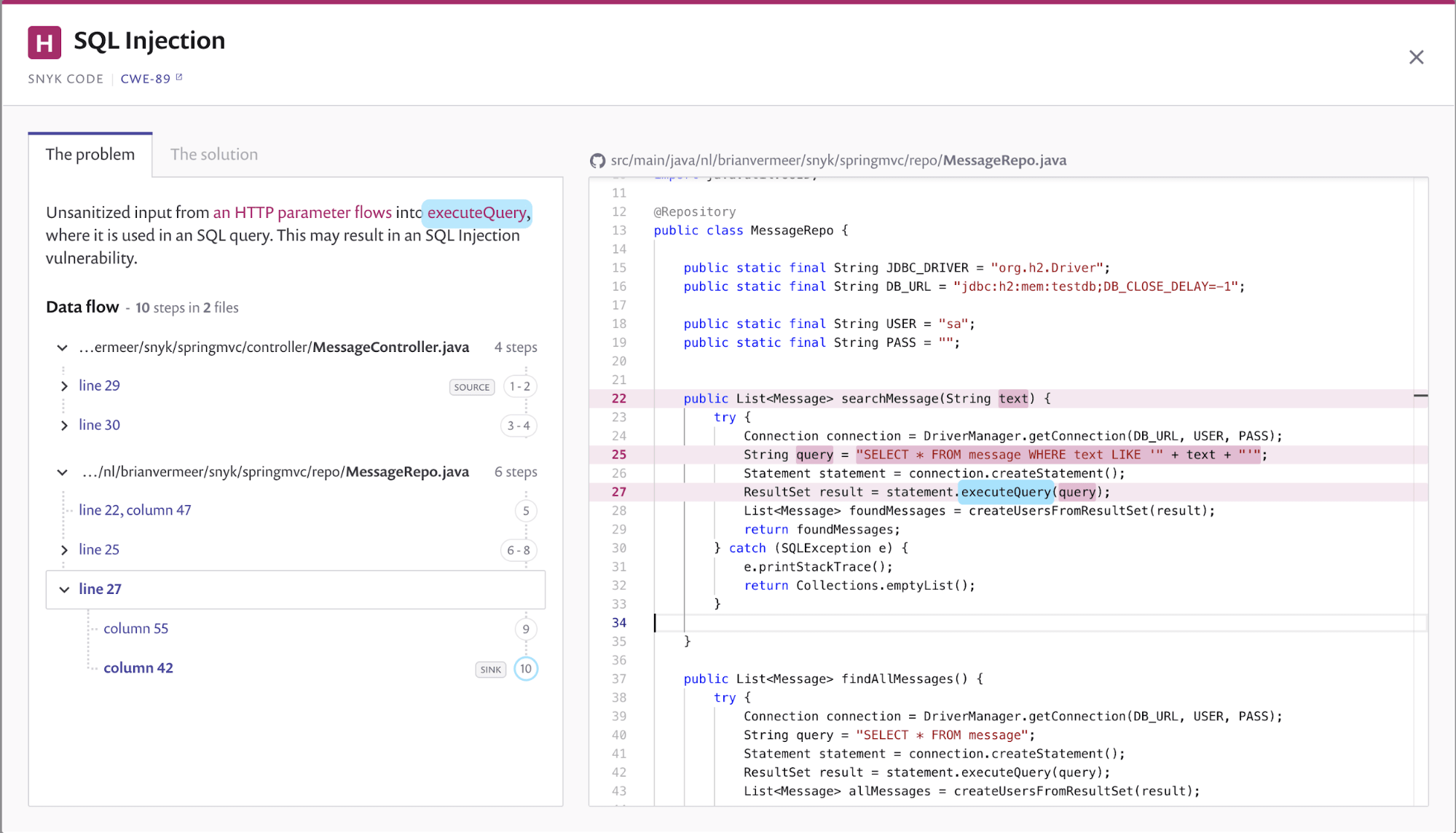
Install and config mysql in windows; Developers can prevent sql injection vulnerabilities in web applications by utilizing parameterized database queries with bound, typed parameters and careful use of. Another option when it comes to preventing sql injection in java is using java persistence query language, or jpql.
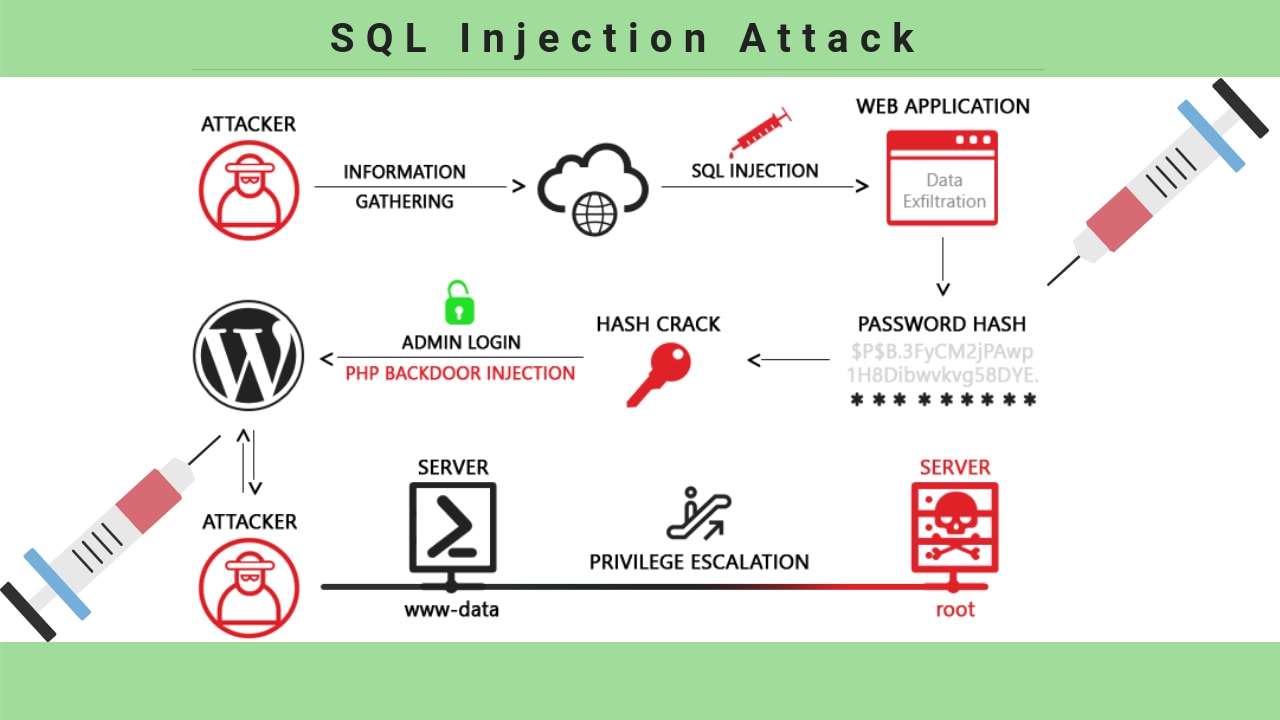
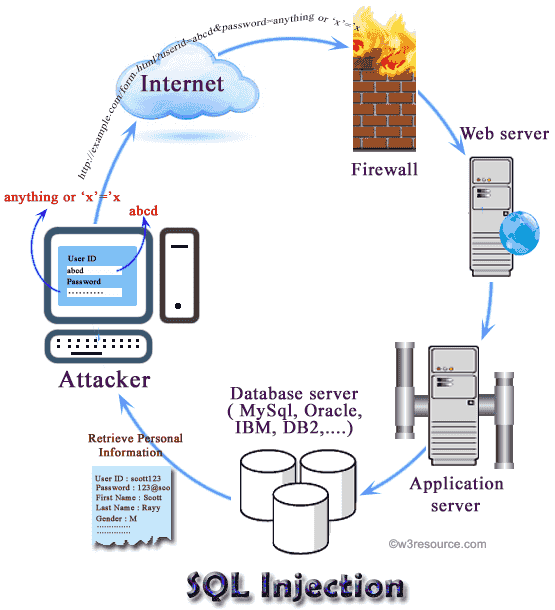
The most important way to prevent sql injection is to avoid vulnerable code and insecure coding practices. An injection attack uses available paths to retrieve data from the database, and either hijack or attack the integrity of the data. Uninstall mysql in linux centos;
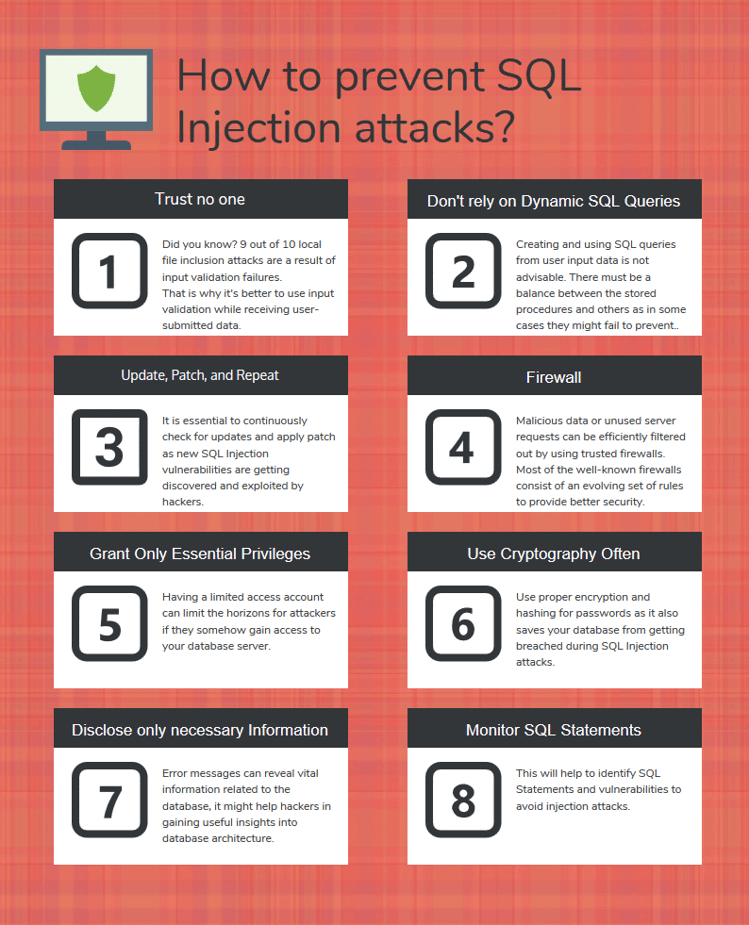
We suggest the following techniques to minimize the risk 1: Validate data before using them in the query. Sql injections have been around for a while now, but they are still a common threat and remain a top database security priority.
Most programming languages that we use to build the frontend have inherent validations and. To prevent sql injection, we need to verify all the inputs before they are sent to the database. There are several implementations of the java.
The following points should be considered to avoid sql injections: Also, it’s better to use the whitelisting technique and patch any vulnerabilities regularly. Remember, sql injections show no physical traces until an attack.